An Encrypted Video Camera: Why & How
Video recordings of police brutality have educated and radicalized citizens for decades. Although people have been documenting police brutality since before I was born, it’s only now — with 21st century technology — that the means of recording this violence are in the hands of nearly every citizen. Widespread and convenient video recording has moved police accountability out of the hands of journalists, and into the hands of the public.
But the current video-recording tools available to the public are lagging far behind what is technologically possible. Protestors and journalists alike do not have easy access to strong encryption. I am presenting here my rationale and design for a secure camera that records encrypted video using off-the-shelf hardware and open-source software.
Surveillance and accountability
Since at least 9/11 America has been a surveillance state. The power imbalance between state surveillance and citizen counter-surveillance has widened into a gaping chasm. The police have their own cameras that they only use as they see fit
- public and private security cameras
- police body cams
- helicopters and drones
- automated facial recognition
- thermal imaging cameras
Ostensibly this surveillance state exists to protect us. We are recorded nearly constantly, and yet when it comes time to hold the police accountable for their crimes, there is always missing footage. Police disable bodycams and destroy recorded evidence. Meanwhile the justice system selectively uses surveillance data and excludes footage that doesn’t fit their prosecutorial narratives.
The surveillance state is a power imbalance that does not serve us. This year I’ve watched protestors, journalists, and organizers try to disrupt this imbalance by recording the violence and cruelty of American police, but it’s been a struggle. When protestors record public demonstrations, they risk becoming another tool in the state’s arsenal. The same way the police can choose when to enable and disable their body cameras, they can choose which footage to steal and misappropriate from protestors. If you have 3 hours of recording that includes both the police tazing a child and a protestor throwing a can of tuna at riot cops, Ii think we all know which footage will make it to the courtroom and which footage is going to get “lost”.”
What tools exist today?
When you choose to record a protest, the footage that you create should be YOURS to decide what to do with. You should be able to choose whether or not anyone else sees it, and you should have the authority to protect the identities of the people you record. As I see it there aren’t a lot of good options available if you want to participate in the counter-surveillance state while retaining authority over and rights to what you record. There are only two widely available tools for video recording:
- A dedicated camera. Here I’m including GoPros, DSLRs, point-and-shoot cameras and camcorders.
- A smartphone running iOS or Android.
Both of these options have serious drawbacks and associated risks.
The risks of video cameras
I can’t find a single manufacturer that offers a video camera with secure storage. OEMs don’t seem interested in providing privacy for their customers. If you use a GoPro to record a demonstration and the police detain you there is nothing stopping them from taking a copy of your recorded video. It’s worth considering the nature of search incident to arrest and the circumstances that determine if the police need to go to a judge to get a warrant. But ultimately we know that, whatever the law might say, the police have no accountability. We cannot trust them, their prosecutors, or judges to follow the law. If you record a protest on a GoPro you should assume the cops can take your footage and use it in any way they see fit.
The risks of smartphones
Recording on a phone has different problems than recording on a dedicated video camera.
All modern iOS devices offer strong privacy through the Secure Enclave. New Android devices use a number of similar technologies under different names. Phones are also just plain convenient. Most people living in the USA own a smartphone of some kind. And as long as your phone stays locked it’s extremely unlikely that the police will be able to access any of your data. I won’t call it impossible since the state has spent a substantial amount of money and research on breaking into mobile devices and i don’t know what they’re currently able to do. But if the state does have the ability to break into a phone it seems like that ability is currently limited to TLAs and high profile cases.
So phones offer substantially more privacy by default than a camcorder or GoPro. But recording on a phone has some major downsides.
- Police can and do track activists using their cell phones. Most organizers recommend that you don’t use your phone at protests. They suggest turning off your phone before you arrive, or leaving your phone at home entirely. Police can and do track activists using their cell phones. If you take their advice seriously, then recording a protest on your phone is already a risk to begin with.
- The police could just take your phone. Who’s going to stop them? Even if the police don’t steal your property, they can’ll happily break it. You might get to keep your data, but paying hundreds of dollars to repair or replace your phone can be anywhere between “not fun” and “life-ruining” depending on your financial situation. Good luck suing the city for damages before 2025.
- If the police do seize your phone, they have some easy ways to unlock it. Current jurisprudence gives cops the freedom to unlock your phone using fingerprint or facial recognition without your consent. Organizers often recommend that you disable biometric authentication on your phone and ONLY use a passcode. The police need a warrant to get your passcode, and even then, you don’t HAVE to give it to them if you’re willing to stand in contempt of court. If you’re using FaceID you’ll have a harder time maintaining your privacy.
- If the police seize your phone AND get access to your data, whether they use legal or illegal means to do so, you suddenly have a much bigger problem. If the police take your GoPro and make a copy of the SD card, that sucks. But if the police take your iPhone and unlock it, now they have access to a treasure trove of data. The 4th amendment jurisprudence surrounding smartphones is weak and it’s unlikely that the police would limit their search to finding only the video you were recording when they arrested you. More likely they will comb through your contacts, your photos, your conversations and your notes, and make copies of whatever they want.
You can protect yourself from most of these problems by using a burner phone. I specifically mean a smartphone that you don’t use for anything except for recording. There’s an enormous market for used smartphones and they’re pretty cheap these days - about $100 for a 4 year old phone. If you disable biometric authentication and turn off all the networking then you’ve got a pretty secure camera.
The device
My prototype device records encrypted video and takes into consideration the current (extra-)legal conditions of anti-police protests. I’m calling it the Comrade Camera (CC).
What does it do
When you turn on the Comrade Camera it automatically begins recording encrypted video to an attached USB drive. Live video is written to the USB drive in 10 second segments. Only the current segment is readable or writable. If the police seize your CC they will only be able to access the most recent 10 seconds of video. As long as the CC has power, it will not stop recording. That means that if the police get your camera they have to turn it off immediately (i.e. under 10sec) if they want access to even the smallest amount of your recording. This might allow police to access the most recent few seconds of video, but it’s better than exposing a multi-hour recording.
How does it compare to cameras/phones?
Dedicated cameras
The only significant downside of dedicated cameras is that they don’t offer any form of encryption. GoPro recordings are stored in cleartext. The CC encrypts your data.
However, the CC has a significantly worse user interface than a consumer device. Most dedicated cameras have well-tested, easy-to-use interfaces whereas the CC does not. It is either on and recording, or it is off.
Smartphones
- Unlike a cellphone the CC doesn’t run any radios. No wifi, bluetooth cell service, GPS - nothing. It should be impossible to track. However I won’t make assumptions about what the government can and cannot do. Use your judgement.
- The CC can be built for about $100. It’s not a huge loss if the cops steal or break it.
- The CC doesn’t use any biometric security. The CC depends on strong, quantum-resistant encryption which can only be unlocked by a secret key that is not stored on the device itself. This probably makes the CC about as secure against 4th aAmendment search-and-seizure threats as a smartphone with a passcode. The court can compel you to share your secret key, but at least the police can’t just unlock it with your face or finger.
- The CC doesn’t have all your personal data on it. If the police gain access to the CC’s filesystem, they’ll find nothing but encrypted video and a stock raspbian install. No email, no contacts, no photos of your family.
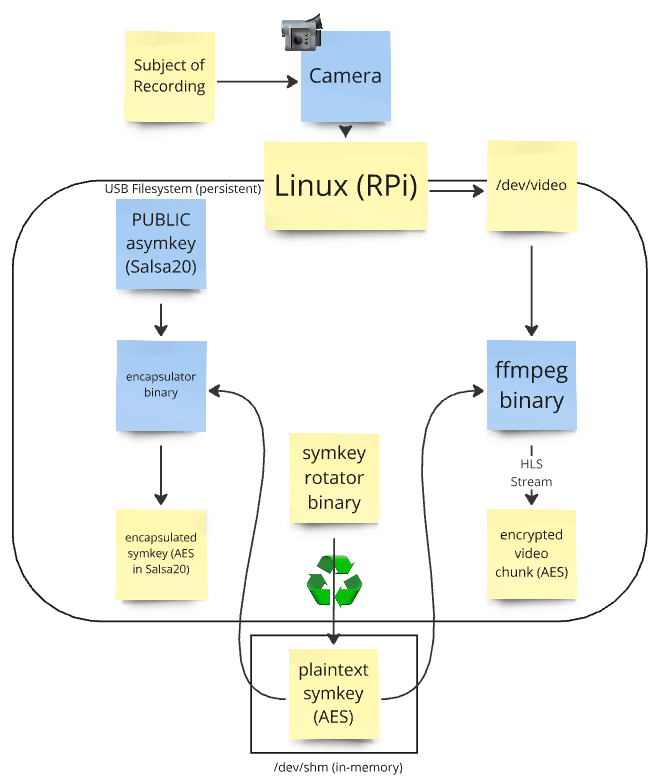
Next Up - Technical Design and Implementation
Stay tuned for a future blog post where I will detail the design of the software and release the full source code. Here’s a sneak peek of the basic design:
Bibliography
4th amendment rights and smartphones
- Vox - The police want your phone data. Here’s what they can get — and what they can’t.
- Motherboard - We Built a Database of Over 500 iPhones Cops Have Tried to Unlock
- USA Today - Can police unlock your phone? Disappearance of NJ woman shows why policy frustrates cops
- EFF - Apple, Americans, and Security vs. FBI
- Cellebrite - Access and Collect data from the widest range of digital devices
- Ars Technica - FBI’s stingray quickly found suspect after local cops’ device couldn’t
- EFF - Search Incident to Arrest
- US Supreme Court via Archive.org - Riley v. California
Advice for using your phone at a protest
- EFF - Surveillance Self-Defense
- The Intercept - Protestors, Here’s How to Set Up a Cheap Burner Phone
- EFF - A Quick and Dirty Guide to Cell Phone Surveillance at Protests
Encryption and dedicated cameras
- TechCrunch - Adding encryption to cameras won’t solve photojournalists’ problems
- The Verge - Filmmakers and journalists ask camera companies to embrace encryption
How cameras can serve the people
- Twitter - recordings of police brutality from @greg_doucette
- EFF - You Have a First Amendment Right to Record the Police
How cameras serve the police
- Business Insider - The FBI said it used Instagram, Etsy, and LinkedIn to track down a protester in Philadelphia accused of setting a police car on fire
- Vice - New Photos Show at Least One Cop in Deadly Breonna Taylor Raid Was Wearing a Body Camera
- WLEX-TV/NBC - Breonna Taylor evidence photos contradict LMPD’s ‘no body cam’ claim
- Vice - New Body-Cam Footage Raises Questions About Breonna Taylor Death Investigation
- CNN - Body cam industry is under pressure after deaths of George Floyd and Breonna Taylor
- Orin Kerr - Can the Police Now Use Thermal Imaging Devices Without a Warrant?
- US Supreme Court - Kyllo v. U.S.
Other tools for police accountability
- ACLU - Mobile Justice CA
- The Verge - Signal announces new face-blurring tool for Android and iOS
- checkthepolice.org via Internet Archive
Examples of police opposition to accountability
- The New Yorker - How Police Unions Fight Reform
- South Coast Today - Police chiefs across state speak out against reform bills
- Nashville.gov - MNPD’s Response to Gideon’s Army Report
Cryptography
https://gist.github.com/atoponce/07d8d4c833873be2f68c34f9afc5a78a https://www.2uo.de/myths-about-urandom/ https://www.youtube.com/watch?v=6gn8AfeRvA8 https://www.youtube.com/watch?v=msPrqDwLhi8 https://qvault.io/2020/09/10/is-aes-256-quantum-resistant/ https://www.raspberrypi.org/forums/viewtopic.php?t=141566 https://www.raspberrypi.org/forums/viewtopic.php?f=63&t=207888
Key generation and storage
Forbes - What Happened When The DEA Demanded Passwords From LastPass